To the Surgeon
Later today I am headed to see my surgeon to schedule a proceedure. I need to have a surgery that is going to leave me off my feet for a week or more. My family will have to pick up the slack at home and my co-workers will have to take on my share of the work. The surgery is disrupting to my life and carries with it a measure of enduring risk. The most troubling thing is it could have been prevented had I adopted some healthier habits earlier in life. An ounce of prevention is worth a pound of cure.
SOAR is Reactive : Surgery
I find myself regularly in conversations about the SOAR capabilities of WitFoo Precinct. Our product does a great job at providing automation where and when it is needed. The caution I give my cybersecurity heroes is that SOAR should only be used as sparingly as surgery would be in the healthcare domain.
As we work with customers with our partners, we strongly encourage this approach:
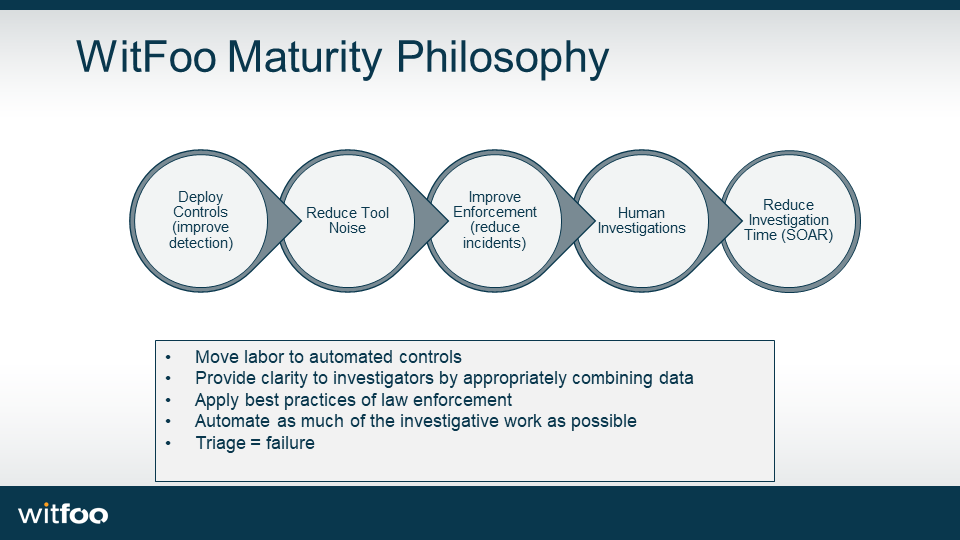
Step 1: Tool Up
The Center for Internet Security (CIS) maintains the Critical Security Controls (previously SANS.) It can be inspected here: https://www.cisecurity.org/controls/. The Critical Security Controls is a listing of the most important and basic controls (security tools) in the craft. Every control in CIS CSC are in every framework including NIST, ISO, PCI, HIPAA & FEDRAMP. If you do not have the critical/basic controls in place, it makes no sense to do advanced controls like SOAR. It would be as reckless as having a monthly visit for liposuction without adjusting diet and exercise.
CIS has tools online to perform your own assessment of compliance. The video below shows how WitFoo Partners utilize Precinct to assist in performing those ongoing assessments.
Step 2: Tune Tools
Buying a gym membership will not make you healthier if you don’t make good use of it. The same is true of securing an organization by purchasing the Critical Security Controls; they must be effectively deployed.
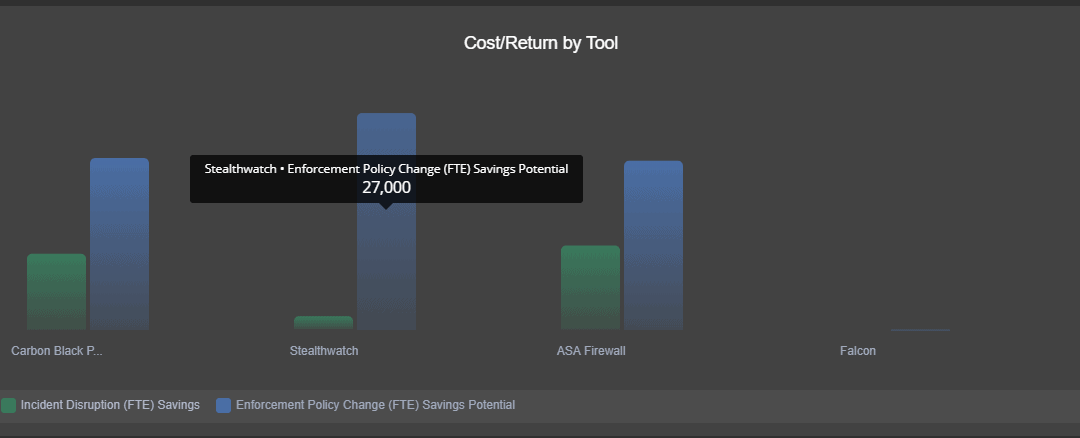
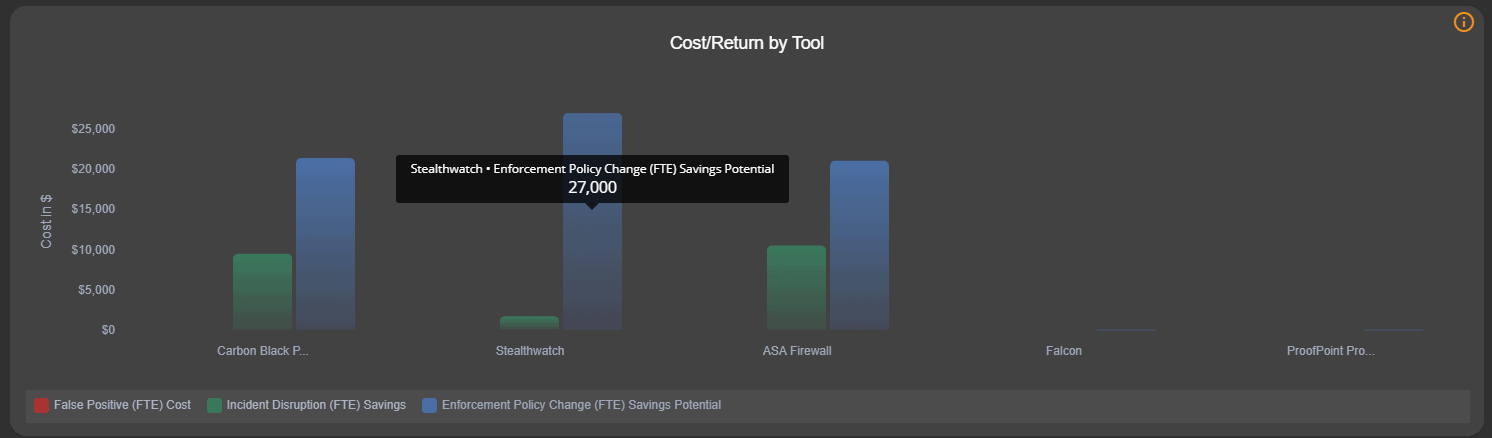
The graph below is from WitFoo Precinct. The blue graph bar shows real incidents being detected by the referenced tool but the incidents are not being blocked/disrupted. It is a clear symptom of under utilized technology. These systems need to be fully configured to deliver value to the organization or the security cycle becomes reactive (using SOAR.)
Step 3: Incident Response with SOAR
As WitFoo Customers work with our Partners to execute a maturity path to make the security architecture secure, the number of real incidents that are not automatically stopped by early stage tools is reduced to nearly 0 each month. This is accomplished by applying orchestration and automation to all phases of the investigation.
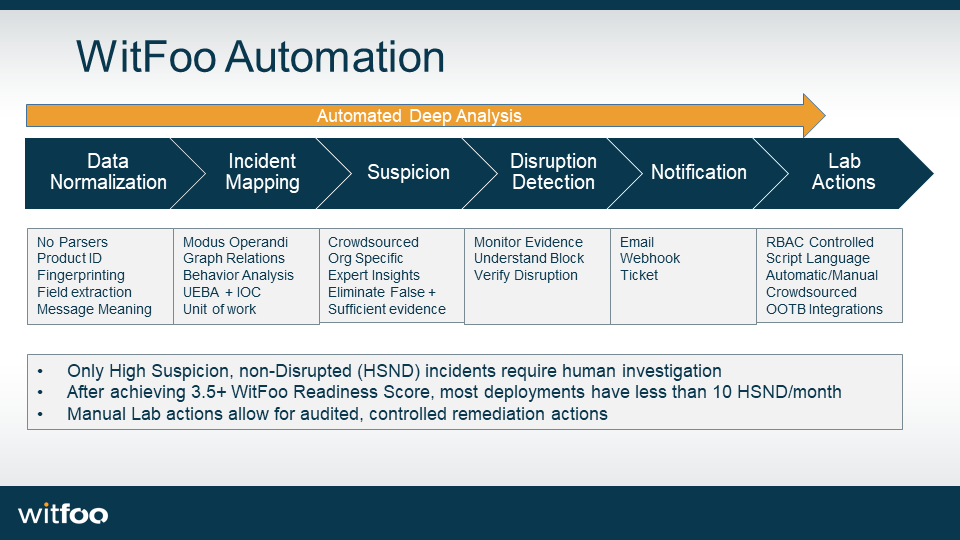
The Place & Benefit of SOAR
As part of a holistic, healthy security practice, SOAR can provide a ton of benefits to the security team. If it is over used or used in lieu of a heathy security practice, it will make things worse.
I recently was having beers with the security team from a Fortune 500 Manufacturer that had gone down the path of SOAR (not using WitFoo) a few years ago. They now have over 100 scripted “playbooks” created and maintained by 3 full time employees (with 2 empty billets.) As the automation has become more complicated, the errors have become more frequent and disruptive to business. Their practice is under extreme scrutiny as a result. The directive from the CIO is to “make things healthy, be more proactive and less reactive.”
Change Controls
Response scripts & playbooks can be extremely useful in a healthy security practice. To accomplish this, the scripts should be reviewed using the same scrutiny of change controls that re-configuring a firewall would have. This often being skipped, however.
One of the main drivers in going to a SOAR first approach is that it doesn’t require the red tape of broader IT and business. The SECOPS team can get things done more quickly by creating scripts that will only be executed in emergencies. The problem becomes that the “emergencies” happen dozens of times an hour. The end result is marginalization of the security team paralyzing them in the future.
WitFoo Philosophy: Health First
As mentioned in the opening, SOAR is an advanced tactic that should not be put in place until basic controls are deployed properly. No organization should be executing automated surgery several times a day without a plan to move to a healthier footing.
Rules of Engagement
Military veterans know that before you pull a trigger certain conditions must be met. Anyone that has watched the Gene Hackman and Denzel Washington classic, Crimson Tide, can remember the entire plot revolved around these rules of engagement. When establishing SOAR playbooks and scripts, the broader business needs to understand the impact of executing those actions. The rules of execution need to be approved by the business. The rules include 1) conditions to execute 2) approval authority for execution 3) controls to prevent erroneous execution and 4) reporting on the execution.
SOAR is not just a security tool. It is a business tool that effects all aspects of business and require the broader business be a part of the conversation.
Stabilizing the Conversations
In my earlier entry Failure Reports, I explain the importance of translating security data into business metrics. The business needs to understand the cost, benefit and risk of SOAR. It also needs to understand why $200k needs to be spent on a new tool or why $50k should be spent on tuning services to extract additional value from the existing tools. WitFoo Partners work with our customers to deliver this value. An outline of the telemetry we create can be viewed in the video below.
SOAR holistically
As a final caution, SOAR is at its most dangerous when it is performed without sufficient data. WitFoo Precinct orchestrates and automates security workflows starting when raw data is received. All data is automatically normalized, analyzed and examined against the best practices of cyber security and law enforcement principles. When WitFoo operators decide to take action against the security architecture, they are armed with all available data and intelligence. Once action is taken, after action reports are created and the security architecture is improved to prevent the same type of failure condition again in the future.
SOAR is an important part of a security practice in the same way surgery is an important part of healthcare. When SOAR is used to bypass business process and controls or is done before basic security best practices are put in place, the organization will end up in a worse place than it was without SOAR.
An overview of Precinct SOAR capabilities are below. Please use responsibly.