WitFoo Precinct can be deployed as an All-in-One Appliance for organizations with less than 1 million events per hour or can be deployed in a horizontally & vertically scaling architecture to allow for millions of events per second and long term retention and processing.
Deployment Video Guide
Deployment Options
WitFoo Precinct can be deployed in several methods.

- Hypervisors: Use the OVA/VHD downloads under Downloads on this page.
- Cloud Hosted: Launch from the AWS Marketplace, Azure Marketplace, or Oracle Marketplace Pricing can be hourly (pay-as-you-go) or BYOL.
- Precinct Cloud: WitFoo’s SaaS offering, where we provide the software and VM infrastructure for a monthly (or pre-paid annual) fee.
- Custom Build: Custom builds on physical or virtual appliances can be achieved via Ubuntu debian installer.
- Managed Service: WitFoo Partners provide managed services for WitFoo Precinct including CyberOpz.
- Physical Appliance: Available from Roqos.
Licenses
A 30 day trial license is automatically issued on all new appliance deployments when they launch. To obtain a trial license manually, please fill out this form. To obtain a production license, please request a quote and a WitFoo Partner will deliver the quote. Cloud hosted licensing on pay-as-you-go appliances are automatically billed to the cloud account. Pricing details are available on the pricing page for software only and the cloud page for SaaS offering.
Appliance Nodes
WitFoo Precinct is deployed via appliance nodes. There is an All-in-One appliance that contains all three WitFoo Precinct components. Each node can handle up to 1 million records per hour when clustered (at optimal resource allocation and Core processing level.) Appliance CPU and RAM must comply with the chart below and must be adjusted on OVA import.
- All-in-One – Contains Investigative Engine (IE), Streamer and Data nodes. Rated up to 1M eph.
- Investigative Engine (IE) Node – Provides the user interface and centralized configuration as well as distributed processing and analysis.
- Streamer Node – Receives, parses, and stores Syslog and NetFlow in a WitFoo Artifact in Data Nodes. Also includes the Investigative Engine.
- SaaS Streamer requires more resources for CPU and RAM due to added Dispatcher functionality.
- Data Node – Cassandra data cluster node to receive, store and process WitFoo Artifacts and Relational (SQL) data cluster.
For additional performance and scale guidance please refer to this training module: https://vimeo.com/277872139.
Appliance Deployment Instructions
- Virtual Machine Downloads
- Amazon Web Services Marketplace
- Microsoft Azure Marketplace
- Oracle Cloud Marketplace
- Custom build on Ubuntu 18.04 LTS (Virtual or Physical) (using Debian installer)
It is highly recommended that appliances be thick provisioned to prevent performance and stability issues.
For more appliance installation and configuration guidance see: https://community.witfoo.com/forums/forum/virtual-appliance-and-os/
Network Configuration
The operating system of WitFoo Precinct is Ubuntu 20.04 LTS. Before running ./register ensure networking is configured correctly. For reference see: https://ubuntu.com/server/docs/network-configuration
It is highly recommended that network configuration be handled through DHCP scope reservations.
Installation Walk-through
The Deployment Checklist can be accessed at: https://community.witfoo.com/forums/topic/witfoo-precinct-deployment-checklist/
Firewall Ports
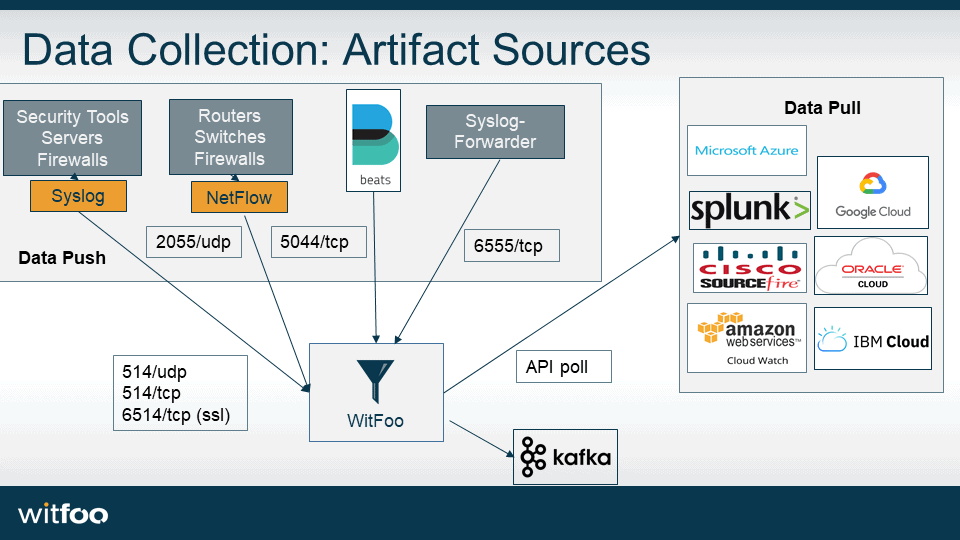
All appliances must be able to reach the following external hosts on HTTPS (443/tcp):
Additionally, the cluster communicates internally over the following ports.
| Image | Open Ports |
|---|---|
| All-in-One | SSH (22/tcp), HTTPS (443/tcp), Syslog (514/udp/tcp, 6055/tcp, 6555/tcp), NetFlow (2055/udp), Beats (5044/tcp) |
| IE Node | SSH (22/tcp), HTTPS (443/tcp), API (8080/tcp) |
| Streamer Node | SSH (22/tcp), Syslog (514/udp/tcp) Syslog SSL (6514/tcp), NetFlow (2055/udp), Beats (5044/tcp) |
| Data Node | SSH (22/tcp), Cassandra (9042/tcp) Replication (7001/tcp) |
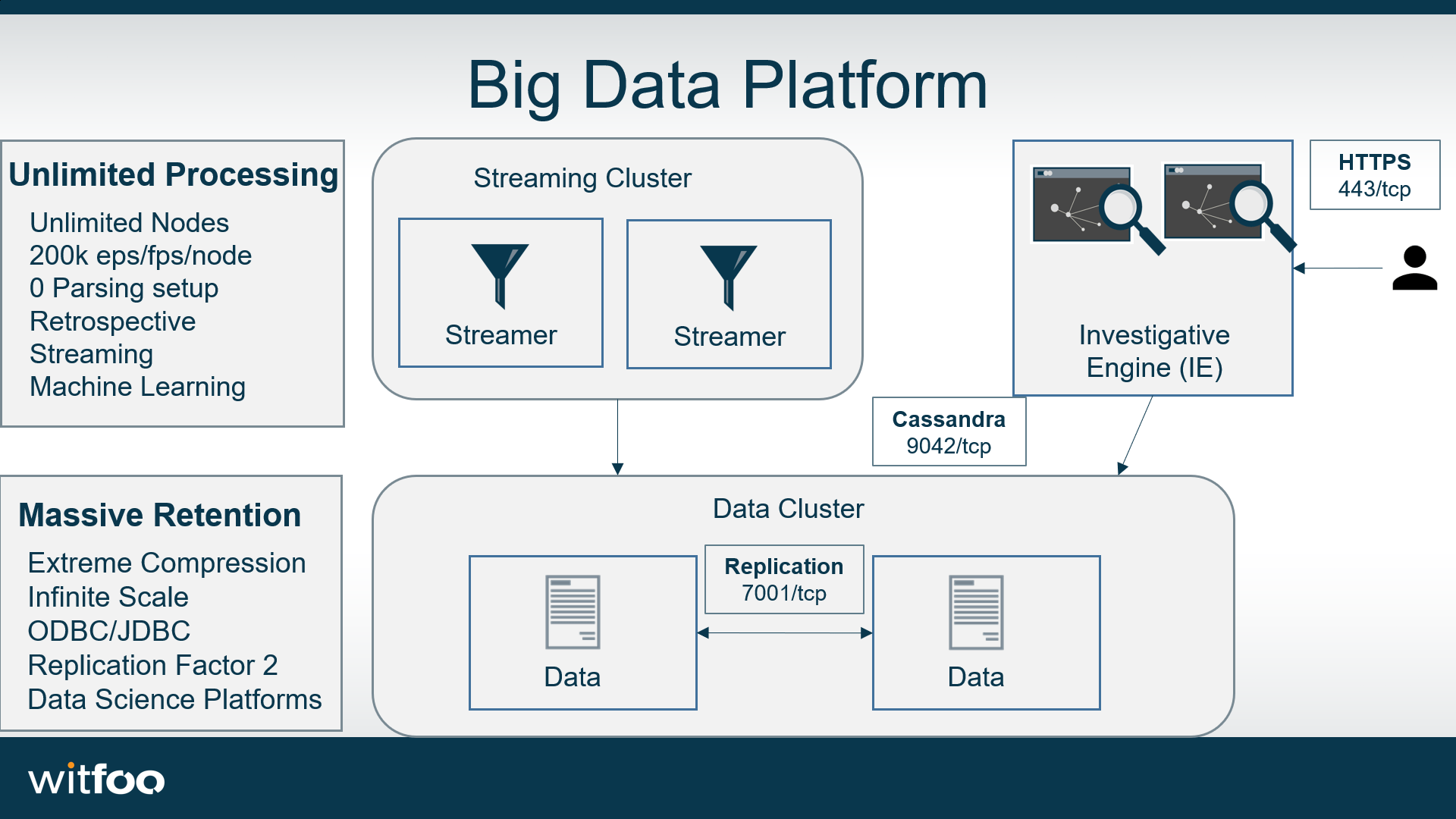
Precinct Architecture
Training
Detailed training on deployment, configuration and scale can be found at: https://community.witfoo.com/courses/ (free registration required.)
Security Products Currently Supported
| Vendor | Product | Critical Security Controls | Guide | |
|---|---|---|---|---|
 | AT&T | AT&T Arris Gateway | 9 ,12 | |
 | Actifio | Actifio | 1 ,2 ,3 ,5 ,11 | |
 | Akamai | Akamai SIEM Integration | 12 | |
 | Amazon Web Services | Cloudwatch | Guide | |
 | Amazon Web Services | Cloudtrail | ||
 | Amazon Web Services | Guard Duty | 9 ,12 | |
 | Amazon Web Services | AWS VPC Security | 9 ,12 | |
 | Amazon Web Services | AWS Instance Backup | 10 | |
 | Apache | Apache Web Server | ||
 | Apache | Apache Tomcat | ||
 | AudioCodes | Mediant Media Gateway | 9 ,12 | |
 | Automox | Automox | 1 ,3 ,8 | |
 | BRO IDS | BRO IDS | ||
 | Barracuda | Barracuda WAF | 12 | |
 | Barracuda | Barracuda CloudGen Firewall | 9 ,12 | |
 | Barracuda | Barracuda ESS | 7 | |
 | Beyond Trust | Beyond Trust | 4 ,16 | |
 | Carbon Black | Carbon Black Protect/Defend | 1 ,8 | |
 | Centrify | Centrify | 4 ,16 | |
 | Checkpoint | Checkpoint FW | 9 ,12 | Guide |
 | Checkpoint | Harmony Email | 7 | |
 | Cisco | Firepower | 9 ,12 | Guide |
 | Cisco | Cisco Ironport | 7 | |
 | Cisco | Cisco Threat Response | 1 ,8 | Guide |
 | Cisco | Cisco Wireless | 15 | |
 | Cisco | Cisco ISE | 1 ,4 ,9 ,14 | |
 | Cisco | Cisco Network Operating System | 11 | |
 | Cisco | Web Security Appliance (WSA) | 1 ,8 | |
 | Cisco | Access Control Server (ACS) | 1 ,4 ,6 ,9 ,11 ,14 | |
 | Cisco | Cisco Meraki Firewall | 9 ,12 | |
 | Cisco | PIX Firewall | 9 ,12 | |
 | Cisco | Stealthwatch | 8 | Guide |
 | Cisco | Advanced Malware Protection (AMP) | 1 ,8 ,3 | Guide |
 | Cisco | ASA Firewall | 9 ,12 | Guide |
 | Cisco | Meraki | 9 ,12 ,15 | Guide |
 | Cisco | Umbrella | 1 ,7 | Guide |
 | Cisco | Duo | 1 ,4 ,9 ,14 | |
 | Citrix | Netscaler | 9 ,12 | |
 | Crowdstrike | Falcon | 1 ,2 ,8 ,3 | Guide |
 | Cubro | Cubro Network Visibility | ||
 | CyberArk | CyberArk EPM | 4 | Guide |
 | CyberArk | CyberArk Vault | 4 | Guide |
 | Cybereason | Cybereason | 1 ,8 | |
 | Cylance | Cylance Protect | 1 ,8 | Guide |
 | Datto | Datto RMM | 1 ,8 | |
 | Deep Instinct | Advanced Endpoint Security | 1 ,8 | |
 | Druva | Druva | 4 | Guide |
 | ESET | ESET Antivirus | 1 ,8 | |
 | Ericsson | Security Manager | 1 ,8 | |
 | F5 | ASM | 7 ,9 ,12 | Guide |
 | FireEye | FireEye Email Security (EX Series) | 7 | |
 | FireEye | FireEye Network Security (NX Series) | 1 ,8 | |
 | FireEye | FireEye Endpoint Security (HX Series) | 1 ,8 | Guide |
 | FireEye | FireEye Malware Analysis (AX Series) | 1 ,8 | |
 | FireEye | FireEye File Protect (FX Series) | 13 | |
 | FireEye | FireEye Central Management (CM Series) | 1 ,8 | |
 | Fortinet | Fortigate | 9 ,12 | |
 | Fortinet | Fortimail | 9 ,12 | |
 | Gigamon | Gigamon GigaVUE | ||
 | Gin | Gin Access Log | ||
 | HAProxy | HAProxy Load Balancer | ||
 | HPE | HPE Nimble | 13 | |
 | HPE | HPE EFS | 13 | |
 | IBM | QRadar | 6 ,16 | Guide |
 | IBM | IBM i Powertech SIEM Agent | 4 ,5 ,14 | |
 | Imperva | SecureSphere | 13 | |
 | InfoBlox | InfoBlox | 1 ,7 | |
 | Infocyte | Infocyte Hunt | 1 ,8 | |
 | JavaMelody Project | JavaMelody | ||
 | Juniper | Juniper FW | 9 ,12 | |
 | LimaCharlie | LimaCharlie | 8 | Guide |
 | Linux | NameD | ||
 | Linux | SSHD | ||
 | Linux | fail2ban | 4 | |
 | Linux | Auditd Logs | 4 ,5 ,14 | |
 | Linux | Linux PAM | 4 | |
 | Malwarebytes | Malwarebytes Anti-Malware | 1 ,8 | |
 | ManageEngine | ManageEngine ADManager | 4 ,14 ,16 | |
 | McAfee | McAfee Web Gateway | 9 ,12 | |
 | McAfee | McAfee ePolicy Orchestrator | 1 ,8 | Guide |
 | McAfee | McAfee Network Security | 9 ,12 | |
 | McAfee | McAfee Endpoint Security | 1 ,8 | |
 | Microsoft | Windows Logs | 4 ,5 ,14 | Guide |
 | Microsoft | Windows Active Directory | 4 ,5 ,14 | Guide |
 | Microsoft | Advanced Threat Analytics | 1 ,8 | |
 | Microsoft | DHCP | ||
 | Microsoft | Azure Security | 2 ,4 ,5 ,9 ,13 ,14 ,16 | Guide |
 | Microsoft | Graph | 2 ,4 ,5 ,9 ,13 ,14 ,16 | Guide |
 | Mimecast | Mimecast | 7 | |
 | Mist | Mist Wireless | 15 | Guide |
 | Mojo | Mojo Wireless | 15 | |
 | Multiple | NetFlow v5, v7, v9 | Guide | |
 | Multiple | IPFIX | ||
 | Multiple | Common Event Format (CEF) | ||
 | Multiple | Log Event Extended Format (LEEF) | ||
 | NXLog | NXLog | ||
 | Netscout | Netscout | ||
 | Netskope | Netskope | 8 | Guide |
 | Netwrix | Stealthbits | 4 ,13 ,16 | |
 | Nokia | NetGuard | 9 ,12 | |
 | Noname Security | Noname Security | ||
 | OPNSense | OPNsense Firewall | 9 ,12 | |
 | OSSEC | OSSEC | 1 ,8 | |
 | Okta | Okta | 4 ,16 | |
 | OpenVPN | OpenVPN | 9 ,12 | |
 | POSTFIX | POSTFIX | ||
 | Paessler | PRTG Network Monitor | 1 ,6 | |
 | Palo Alto | PAN NGFW | 9 ,12 | Guide |
 | Palo Alto | Cortex XDR | 1 ,2 ,8 | Guide |
 | ProofPoint | Protect | 7 | |
 | ProofPoint | CASB | 7 | |
 | Pulse | Pulse Secure | 4 ,16 | |
 | Qualys | Vulnerability Management | 1 ,2 ,3 ,5 ,11 | Guide |
 | Radware | Radware Appwall | 12 | |
 | Roqos | Roqos Core | 9 ,12 | |
 | SSSD Project | System Security Services Daemon (sssd) | 4 | |
 | SecureCircle | SecureCircle | 5 ,13 ,14 | |
 | Secureworks | Taegis VDR | 1 ,8 | |
 | Security Onion Solutions, LLC | Security Onion | 1 ,6 ,16 ,19 | |
 | Senhasegura | Senhasegura PAM | 4 | |
 | SentinelOne | SentinelOne | 1 ,8 | |
 | Shibboleth | Shibboleth IDP | 4 ,16 | |
 | Solarwinds | N-Central | 1 ,8 | |
 | SonicWall | SonicWall Firewall | 9 ,12 | Guide |
 | Sophos | Sophos Central | 1 ,8 | |
 | Splunk | Splunk | 1 ,6 ,16 ,19 | |
 | Suricata | Suricata IDS | ||
 | Symantec | Symantec Endpoint Protection | 1 ,8 | Guide |
 | Symantec | Symantec Data Loss Prevention | 13 | |
 | Symantec | ProxySG | 1 ,7 | |
 | Tanium | Tanium | 1 ,8 | |
 | Taxii | STIX/Taxii | Guide | |
 | Tenable | Vulnerability Management | 1 ,2 ,3 ,5 ,11 | Guide |
 | Threatmetrix | Threatmetrix | ||
 | Thycotic | Secret Server | 4 ,16 | Guide |
 | Tippingpoint | Tippingpoint IPS | 9 ,12 | |
 | Titan | SpamTitan | 7 | |
 | TrapX | TrapX | ||
 | Trend Micro | Trend Deep Security | 1 ,8 | |
 | Tufin | Tufin SecureTrack | 9 ,11 | |
 | Ubiquity | Unify Security Gateway | 9 ,12 | |
 | VMWare | VMWare VCenter | 2 | |
 | VMWare | VMWare NSX Firewall | 9 ,12 | |
 | Varonis | DatAdvantage | 13 | |
 | Vectra Networks | Cognito | 8 | |
 | VyOS | VyOS | 9 ,12 | |
 | Wazuh | Wazuh | 1 ,8 | Guide |
 | Websense | Websense | 7 ,9 ,12 | |
 | WitFoo | Precinct | 1 ,6 ,16 ,19 | |
 | WitFoo | WitFoo IOC Feed | ||
 | Zix | Secure Cloud | 7 | |
 | Zix | AppRiver | 7 | |
 | carson_saint | Carson & Saint | 1 ,2 ,3 ,5 ,11 | |
 | linux | Uncomplicated Firewall (UFW) | 9 ,12 | |
 | linux | Kernel | 5 ,6 | |
 | linux | Netfilter ulogd | 9 ,12 | |
 | pfSense | pfSense Firewall | 9 ,12 | Guide |
 | zScaler | zScaler NSS | 7 ,9 ,12 | Guide |
