by Charles Herring | Aug 2, 2023 | Artificial Intelligence, blog, InfoSec Craft
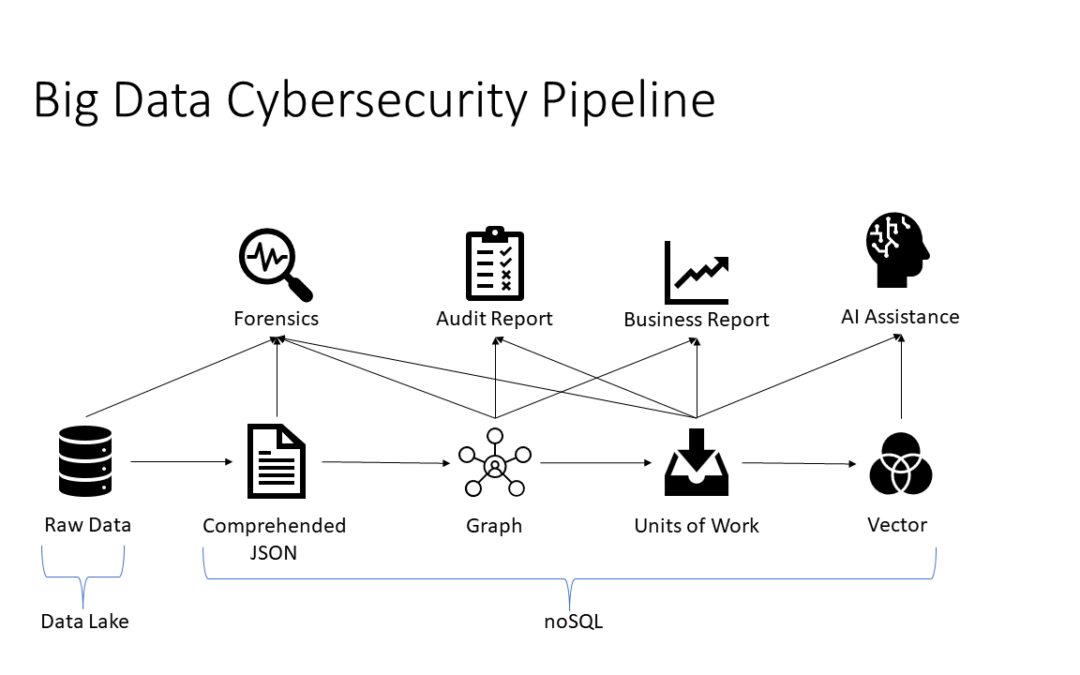
Abstract Building big data pipelines in cybersecurity can solve challenges for incident responders, auditors, executives, law enforcement, MSSP, vendors and other stakeholders. The session will examine approaches to solve for all cybersecurity issues and to enable...

by Charles Herring | May 24, 2023 | Artificial Intelligence, blog, InfoSec Craft
Generative vs. Narrow AI ChatGPT has created a frenzied interest in AI. GPT stands for “Generative Pre-trained Transformer” and is a key innovation in the course of human history. I asked Bing, Powered by ChatGPT, to explain the difference between Generative AI and...

by Charles Herring | May 8, 2023 | blog, InfoSec Craft, WitFoo Story
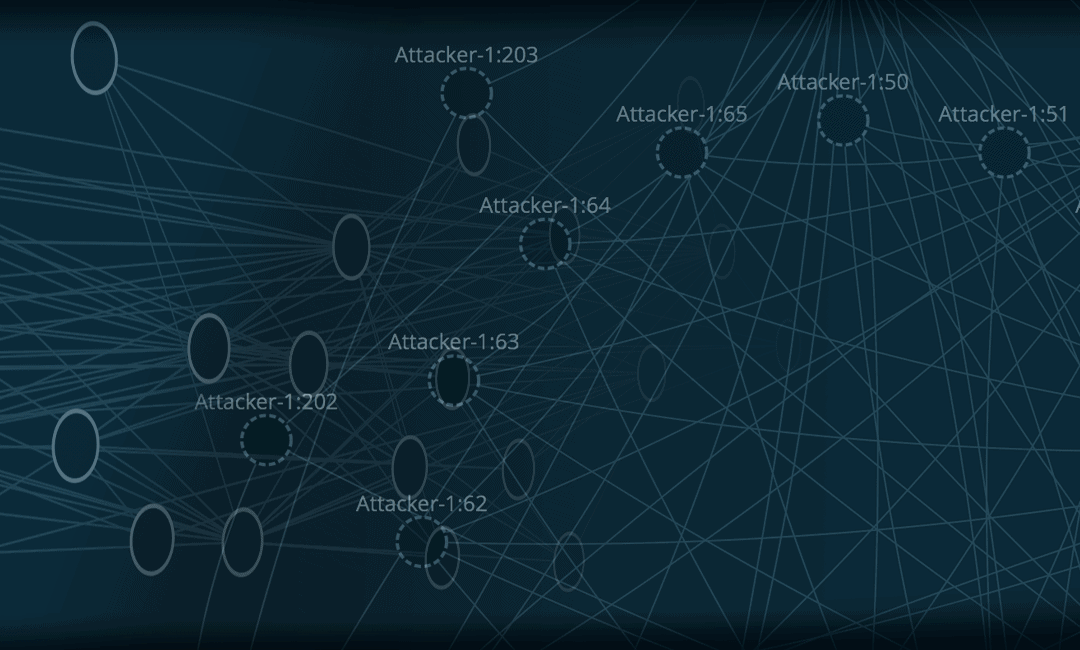
In a 2021 DarkReading article titled Handcuffs over AI, I describe the importance focusing on the outcome of increasing deterence in cybercrime. The presentation can be downloaded here. SECOPS DRIVING CRIMINAL PROSECUTION via a Global CyberGrid At a key point in the...

by Charles Herring | Dec 11, 2022 | blog, InfoSec Craft, Inside WitFoo
The following abstracts are available for delivery at security meetings and conferences. Bio Charles Herring is co-Founder and Chief Technology Officer at WitFoo. WitFoo was founded to enable the sharing of information and operations across the craft of Cybersecurity....

by Charles Herring | Aug 29, 2022 | blog, InfoSec Business
The purpose of a CISO and a cyber program is to reduce the costs associated with cybersecurity. I said this to colleagues at a social mixer this week and their heads almost exploded. “Shouldn’t we be trying to stop and mitigate risk?” “We need to spend more money on...

by Charles Herring | Dec 14, 2021 | blog, Security Breaches
Log4J/LogShell (CVE-2021-44228) exploit IOC have been published by Cisco Talos (see: https://blog.talosintelligence.com/2021/12/apache-log4j-rce-vulnerability.html). These IOC have been packaged as a WitFoo Actor definition and have been pushed to all production...