In a previous entry, I spoke about the difference between a mature craft (like aviation) and information security, or the latest sexy title “Cybersecurity”. Reflecting on what I just said… the mere fact that the name of this discipline keeps changing is indicative of an infantile craft. Information Security (INFOSEC), Computer Security, Network Security, Information Warfare (IW), Information Dominance (ID) and now Cybersecurity (which wasn’t even a word). Ok, so I borrowed some terms from the navy (IW and ID) – these terms include the craft I am speaking of, so I took some latitude.
Public & Private Sector organizations are facing a relentless storm of cyber-attacks that cannot be stopped by enforcement tools and software alone. This requires reactive incident response teams (IRT) to detect, investigate and contain security breaches as they occur. The challenges facing these teams include thousands (or millions) of events being generated daily that need to be investigated and the information they require being distributed across multiple tools. This leaves even the largest organizations in a state of systemic failure when required labor hours are many times greater than available labor. This leads to protracted departmental failure and high organizational risk to cyber breach.
I don’t think anyone would argue that cybersecurity is a mature craft. I would certainly argue that aviation is a mature craft, or discipline. Examples of this are illustrated by describing the cockpit and explaining the efficiency achieved by relative position to the pilot, mechanism for attention required and ease of information consumption. There are many things a pilot must keep track of and there are elements of criticality and timeliness that drive the design of a cockpit and instrument panel. A pilot processes information by viewing instruments and indicators in a sequence called a “scan”. Some information must be referenced faster than a second by second basis and corrections are constantly applied. Altitude, airspeed, and heading are the most time sensitive information to process for obvious reasons of safety and flight navigation. Other, less timely (or less frequently referenced) information such as engine temperature, fuel state, cockpit pressurization, or radio frequencies have varying criticality. Through maturation, when criticality of a status indicator is high, there is a secondary mechanism to alert the pilot of unsafe conditions. This is usually done with a sound, light or both bringing the urgency instantly to be dealt with.
One critical activity for a naval aviator is the carrier landing. This is the most representative example in aviation of noise elimination and efficiency for achieving a desired result. Landing on a carrier culminates during the last 15 seconds. There are only three things providing information to the pilot which are viewable in a proximity such that the pilots eyeballs are moving as little and efficiently as possible. The three data points being delivered are airspeed, glideslope and approach bearing. Let’s take a deeper look.
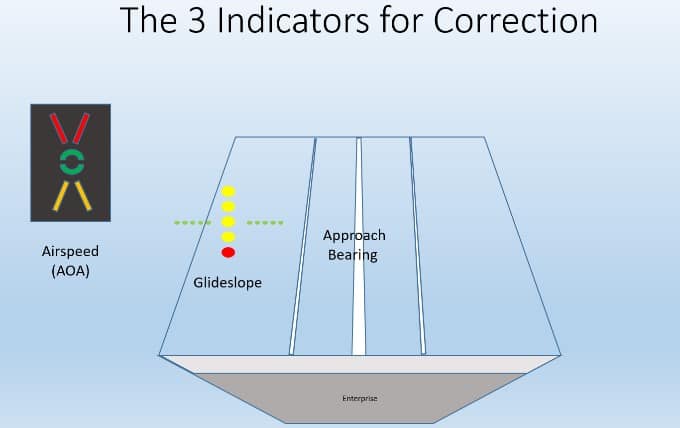
AIRSPEED
This is most accurately measured by the aircraft Angle of Attack (AOA), which is the angle at which the wings are in respect to the airflow. During the landing, the aircraft needs to be flying at the most efficient profile to allow for a minimal airspeed and a maximized aerodynamic response to control inputs. This is called Lift over Drag Max or (L/D)max. The most accurate and sensitive indication when flying at (L/D)max is the Angle of Attack (AOA). A very small change in airspeed is too hard to see on the actual airspeed indicator. The AOA indicator shows this slight deviation in a much more consumable and accurate form. Here is what the AOA indicator looks like:
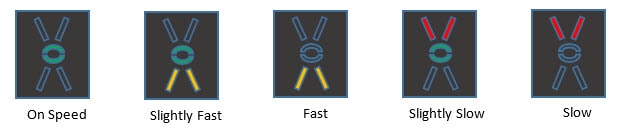
There are some poignant aspects to the AOA indicator.
Color:
Green is an indication of “on speed” (Safe)
Red is an indicator of danger “slow” (dangerous)
Yellow us an indicator of “fast” (Cautious … but less dangerous than slow)
Symbiology:
The green circle is an indication of being correct.
The yellow chevron can be considered a symbol of – pull the stick back… accompanied the color that means to reduce power
The red chevron can be considered a symbol of – push the stick forward… accompanied the color that means to add power
GLIDESLOPE
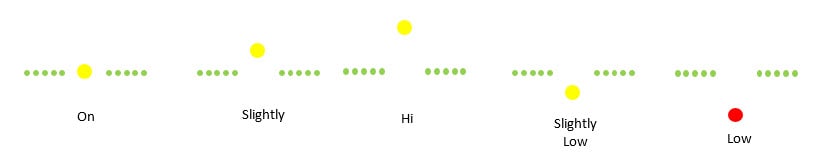
The glideslope indication is accomplished by an Optical Landing System (OLS) (nicknamed “Meatball” or simply, “Ball”). It is a series of lights that show the pilot their position relative to the ideal glideslope. The green lights are called the “datum” and the yellow (or red) light (the Ball) show where the aircraft is relative to the glideslope. If you see the ball below the datum you are low and if you see the ball above the datum you are high. Two balls low turns red and is very dangerous … especially if you are slow! Accurate glideslope combined with being “on speed” will result in an effective arrestment on the carrier with the tail hook catching the targeted wire (the 2nd or 3rd of the 4 wires that are in place).
APPROACH BEARING
The simplest of the three parameters. This visual cue is simply the angel you see the center-line down the landing area of the carrier. If it points right you must come left and vice versa.
Here are some samples of sight picture examples and the corrections required
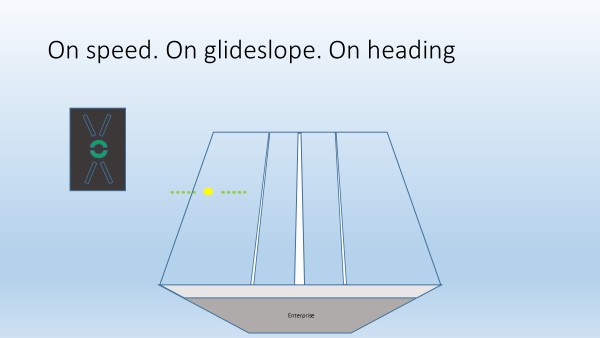 No correction required
No correction required
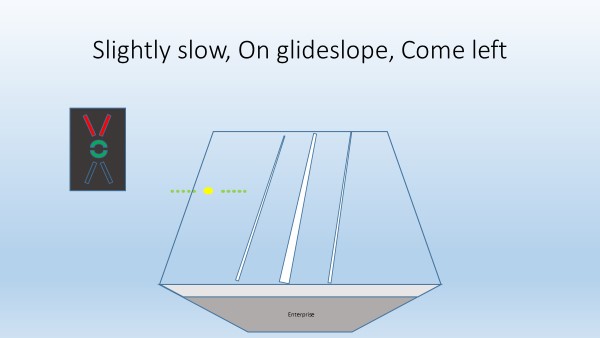 “Come left… little power” might be a LSO call. Deviation is quite small … so silence from the LSO deck would not be unusual.
“Come left… little power” might be a LSO call. Deviation is quite small … so silence from the LSO deck would not be unusual.
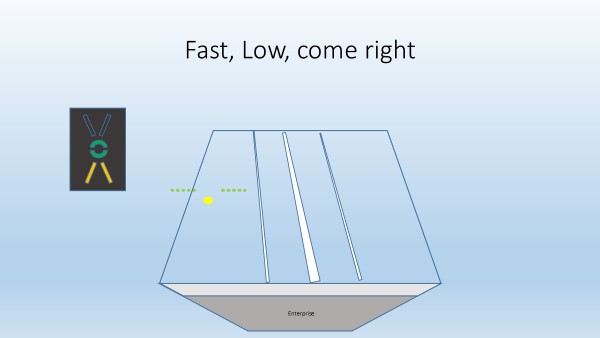 No LSO would call this … the correction is a simple energy transfer from the speed to correct for the glideslope while correcting to the right.
No LSO would call this … the correction is a simple energy transfer from the speed to correct for the glideslope while correcting to the right.
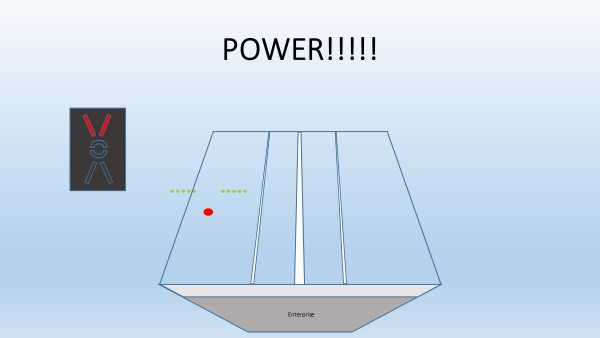 Not a good situation … the LSO would be screaming at you “Power!!! Power!!!”
Not a good situation … the LSO would be screaming at you “Power!!! Power!!!”
Notice the efficiency. The three things the pilot is looking at on final approach are right in front of his face. The pilot’s eyes hardly move at all to see all the information needed to perform one of the most difficult activities in aviation.
Where is this efficiency in cybersecurity or specifically incident response? The disparate tools at the disposal of responders are difficult to use and inconsistent… if they are fortunate enough to have any tools at all. Many of these tools are so expensive, only the cyber privileged (i.e. the Global 2000) have access to them.
I won’t get into naming specific tools but there is a tremendous amount of information generated by network monitoring systems, intrusion detection/prevention systems, firewalls, endpoint detection, vulnerability scanners, DLP systems, etc. All of this information (logs) is relevant and, depending on the size of the organization, can result in thousands or even millions of events/day which require consideration, investigation and analysis. Information Security is evolving but we have a long way to go to reduce the noise and make incident responders more efficient.
Again, it’s been over 20 years since I’ve been in a cockpit but the training I received is still imprinted in my brain. Why is that? Well, my career pivoted into Cybersecurity after my glory days as a Naval Aviator. To this day, I have not had a sequence of training or experience in Cybersecurity the likes of which was instilled in me during my flight training. Reason being, aviation is a more mature and evolved craft and Cybersecurity is not! I now work with an amazing team of very experienced Cybersecurity professionals and our intent is to fix this problem!